
At the Pwn2Own Toronto 2023 security competition at the end of October, the engineering team “Team Viettel” won the championship when completing all seven registration categories, with a score of 30, 12.75 points higher than the runner-up team. .
This is the highest position a team from Vietnam has achieved after many years of participating in world-class competitions. To achieve high scores in each category, the team said they have devised specific strategies, instead of exploiting any vulnerabilities found as before.

Vietnamese engineering team competes remotely at Pwn2Own Toronto 2023. Photo: Uyen Nguyen
This Pwn2Own contest has the theme of attacking a number of smart devices such as phones, routers, and smart equipment systems in offices provided by major companies. Teams will receive an assignment to know which device they will attack and have about three months to find vulnerabilities, write exploit code, before demonstrating the attack for 30 minutes. The target devices are all updated with the latest software.
According to team leader Ngo Anh Huy, the challenge of the competition is that the previous team can exploit the same vulnerability as themselves. At that time, if you take the test later, even if you exploit it successfully, you will not get a perfect score. In addition, challenges also come from the device manufacturers themselves.
“The devices are all at a high level of perfection. The manufacturers are world-leading companies and also always want their devices to be unhackable in the competition. So they will also patch most of them.” hole right before competition day,” Huy said. Last year, the group also lost points for choosing the correct vulnerability that the manufacturer knew about.
The proposed strategy is to find many errors, prioritizing errors that few people discover and exploit. With nearly three months of “eating and sleeping” with the equipment, the Vietnamese engineering team said they had to predict which approaches were easy and that someone would exploit, and which were the difficult approaches that few people knew about. Then they will choose the more difficult direction.
For example, in the smart speaker category, member Do Manh Dung said it took him a week to find a difficult enough vulnerability on the Sonos Era 100 speaker model, and it took two months to write the exploit code. “I am confident of success because this is a very difficult hole to find,” said the team’s youngest member born in 2003.
This strategy of the competition team was effective. At the SOHO Smashup competition, when teams had to attack routers and then attack other devices, Huy said there was a previous team that had a very similar approach to his team.
Because this is also the final test and has the most points, the team said they have prepared three holes. These are all vulnerabilities that few people have discovered and are considered the most difficult to exploit. The group succeeded, despite nearly failing after two botched performances.
The results also helped Team Viettel achieve maximum points in all seven registration categories. Products found to be defective include Xiaomi 13 Pro, QNAP storage system, Canon, HP, Lexmark printers, Sonos smart speakers and SOHO Smashup. The group received a bonus of 180 thousand USD.
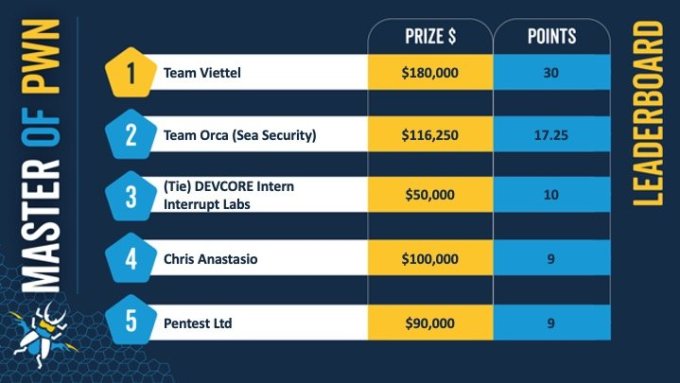
Vietnam’s team ranked first at Pwn2Own for the first time. Photo: ZDI
According to Ha Anh Hoang, an information security engineer born in 1997, due to having to take the exam online, the team may also be at a disadvantage compared to in-person teams in that they can only check the device remotely via camera. “The exam process cannot control technical problems that arise, so we must focus entirely on vulnerabilities to ensure success,” Hoang said.
The group plans to select targets that are rated more difficult in the following competitions, such as Apple iPhone and Google Pixel.
Pwn2Own is the world’s largest and most prestigious cyberattack competition organized annually by Zero Day Initiative since 2007, and is considered the World Cup of the security world. This year’s event has eight categories, including Mobile Phones, Smart Home Controllers, Smart Speakers, Printers, Surveillance Devices, Network Storage Devices, Google Devices, Small Office Devices, with over a million USD in prize money. After the competition, devices with discovered vulnerabilities will have to issue patches within 90 days.
Luu Quy

Leave a Reply
You must be logged in to post a comment.